How do software dependencies affect the development of IT systems?

Definition: Dependencies are technical relationships among code that create and reflect social relationships among individuals, groups, and organizations. Another simple definition: A state in which one object uses a function of another object.
When is optimal time to deal with it: After you gone through and identified certain tasks then you can start considering the various dependencies that may occur.
Types of dependencies:
- Some of those dependencies are based on technology. Example: I first need to have UI/UX Design before building software / web applications or adding new features, some of those are based on people and people's availability in particular.
- Some of the dependencies are mandatory because they have to happen. Example: I have to have code before I can test.
- Some of those are discretionary dependencies. Example: it may be more convenient for us to organize the work in particular why.
- Some of these may be external dependencies. Example: our team is one scrum team of many in the scrum of scrums and there may be various inputs we need from other scrum teams in order to be able to carry out our task successfully.
- Last and certainly not least, we may have various internal dependencies among our teams and resources and how we carry out our work.
Answer on the article headline: software dependencies affect the development of systems by creating situations where developers and groups must engage in articulation work, and organizations must participate in social worlds.
Skill families in details

These are the skills that every employer is looking for in the digital age. These skills will be required to thrive alongside disruptive and emerging technologies such as AI and yes, these are the future predicted skills needed!
A dynamic mix of these 6 skills families is important to secure a job or start a business and will be needed to retain a job, grow a business, or navigate to the next opportunity. However, it is important to note that you don’t need to have all the skills under a skilled family to be successful!
Once you know what you’re interested in, it’s worth researching more about it. Make use of online resources such as training courses, video tutorials, podcasts, or blogs wherever possible. A mentor or job advisor could also help you identify the best ways to learn your relevant specialized skills.
Please look at this list:
Artificial Intelligence for beginners

AI will not replace humans in the workforce. Human augmentation (machines helping humans) will lead to new, fast and smart ways of working.
Humans will also be needed to improve the performance of intelligent technologies as well as take on other higher value and interpersonal responsibilities which machines are incapable of doing (e.g. creativity, improvisation, dexterity, judging, social & leadership skills, etc).
Machines are really good at repetition, speed & prediction which is where we can benefit from their strengths!
The full promise of AI depends on humans and machines working collaboratively (the collaborative intelligence) to develop differentiated customer experiences and create entirely new products, services and markets.
That is the real opportunity of AI. So lets start from the beggining.
First part: DEFINITION, ULTIMATE GOAL, WEAK AI, STRONG AI:
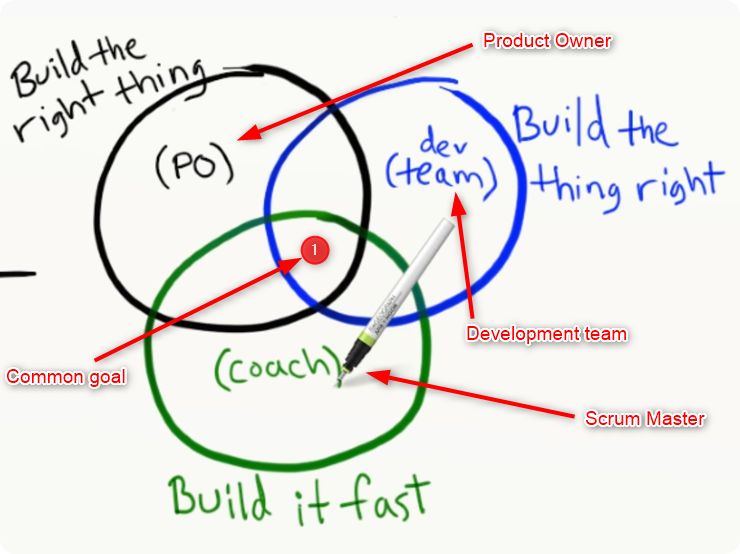
One photo: Scrum team responsibilities
In the Scrum team, who is responsible for:
- Building the right thing?
- Building the thing right?
- Building the thing fast enough?
- What is the common goal?
What Are The Differences Between Project Manager And Scrum Product Owner
If you are interested in knowing what are the differences between a Project Manager and a Scrum Product Owner because they are at the crossroads on choosing to become a Product Owner or Scrum Master. In this video, Joshua Partogi shared the differences between the two roles.
Guess who initiated this thread? :)
Solve complex problems with a little help of your brain
The reticular Activating systems of your brain will help you to solve complex problems. In this video, you can see free example techniques. If you want to solve a complex problems, you need to hold this problem long enough in your mind so that he triggers Reticular Activator in your brain.
Please see this video and leave feedback:
Scrum Guide 2020 Audio Book and Glossary of Scrum Terms
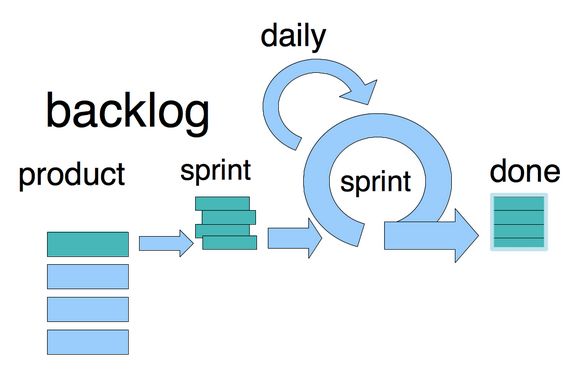
Scrum is a framework for developing, delivering, and sustaining complex products. This Audio Guide contains the definition of Scrum. This definition consists of Scrum’s roles, events, artifacts, and the rules that bind them together. Ken Schwaber and Jeff Sutherland developed Scrum; the Scrum Guide is written and provided by them. Together, they stand behind the Scrum Guide.
I'd like to let you know that the official Scrum Guide 2025 is now live and can be downloaded for free here!!!
Now, you can listen to this Audio Guide by Michael Wisdas while you are driving, just open this page.
Hope you like it:
Agile Retrospectives Done Right
A Retrospective is a Scrum event for your team that reflects on the past to improve the future. Between technical and non-technical teams, you can retro on just about anything! Right now, we're hosting a public retrospective on agile software development. Help define the future of agile by adding some of your ideas to our board.
Microsoft Open Source Application Inspector
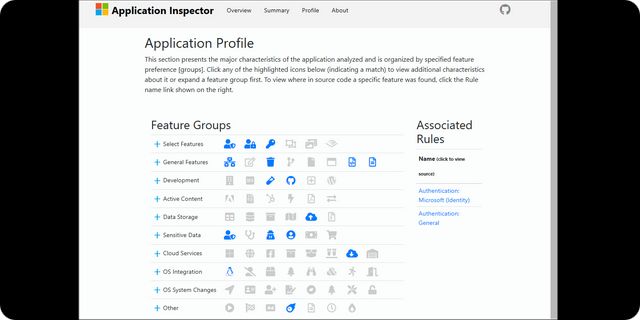
Open-source application from Microsoft Application Inspector is a source code analyzer built for surfacing features of interest and other characteristics to answer the question 'what's in it' using static analysis with a JSON based rules engine.
Ideal for scanning components before use or detecting feature-level changes.
Application Inspector's primary objective is to identify source-code features in a systematic and scalable way not found elsewhere in typical static analyzers. This enables developer and security professionals to validate purported component objectives, eg, a string padding library only does what it says," Microsoft explains in a wiki.
Application Inspector produces a browser-based report that summarizes the major characteristics identified, including application frameworks, cloud interfaces, cryptography, sensitive data like access keys, personally identifiable information, operating system functions, and security features.
What are the 5 stages of team development?
In 1965, a psychologist named Bruce Tuckman said that teams go through 5 stages of development:
- forming,
- storming,
- norming,
- performing and
- adjourning.
The stages start from the time that a group first meets until the project ends. Tuckman didn’t just have a knack for rhyming. (Although, it does make the stages easier to remember.) Each is aptly named and plays a vital part in building a high-functioning team.






