Ransomware is a sophisticated malware that blocks users’ access to their files through the use of encryption. The attackers will ask for a ransom to unlock the infected computer. Although ransomware has been known as a method of attack for a long time, it is still very much in use – there are still no defenses that can 100% eliminate this threat.
The protection against this malware involves a set of security layers. Companies should look towards not only technology, but also people and process-like solutions. The implementation of ISO 27001 can help fight this sophisticated and viral threat to our data.
What is ransomware?
There are several different types of ransomware, but in general terms the characteristics are:
- It uses sophisticated encryption so that the victim can’t unlock it.
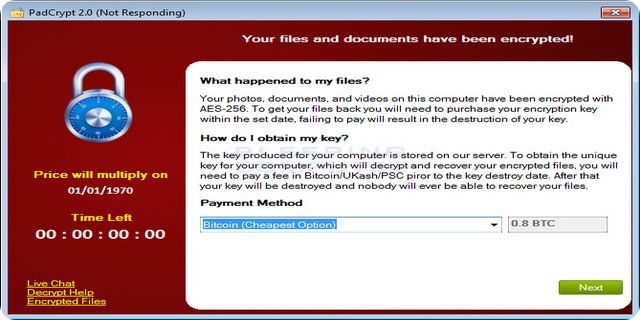
- It displays a message to the victim informing them that their data is encrypted and they will have to pay a fee to be able to recover the files.
- It requests payment in Bitcoins, because this kind of currency cannot be tracked.
- Normally, the ransom has to be paid in a short period of time and increases if it is not fulfilled. Going over the deadline, data will be destroyed.
- Traditional antivirus protection cannot detect this type of malware.
- It can spread to other PCs connected in a local network, network drives, or files stored in the cloud.
The origin of this malware is an organized crime structure that is technologically evolved, and it involves large amounts of money. It is not enough install antivirus software to protect against this threat. Here’s how the ISO 27001 standard can help combat it:
Security layers
The most effective way to be able to combat ransomware, as any malware, is the implementation of security layers that hinder the exploitation of different vulnerabilities that each company can have. Examples of such layers include:
- Security awareness
- Monitoring and event manager
- E-mail, web, and network protection
- Backups
- Updated software and hardware
- Information security policies
- The implementation of ISO 27001 provides a set of controls that cover all of these layers.
ISO 27001 Annex A controls
Annex A contains a list of controls that are selected as a result of the risk assessment, allowing the treatment to mitigate this risk. These are some of the controls that help you protect against ransomware:
- Control A.7.2.2 (information security awareness, education and training) – This control ensures that “all employees receive appropriate awareness education and training and regular updates in organizational policies and procedures.” Without proper training, there is not enough technology resistant to threats of ransomware. The exploitation of this malware can be caused by actions of social engineering, malicious links in e-mail messages, or attachments sent up by known contacts. Employees need to prepare in order to be attentive to these attacks. This means that you have to learn how to perform training & awareness for ISO 27001 and ISO 22301.
- Control A.12.4.1 (Event logging) – As I mentioned, this is a sophisticated malware. The system’s behavior analysis may be crucial for its timely detection. This control suggests not only the creation of event logs, but also regular reviews.
- Control A.12.3.1 (Information backup) – As described in the objectives of this control, “Backup copies …shall be taken and tested regularly.” The ransomware has the ability to spread up to network drives and security copies. Validation of these copies is essential to ensure the success of the restore when necessary.
- Control A.12.6.1 (Management of technical vulnerabilities) – The knowledge of system vulnerabilities is essential to protect against this or any kind of threat. You should learn how to manage technical vulnerabilities according to ISO 27001 control A.12.6.1 to learn more about this control.
- Control A.13.1.3 (Segregation in networks) – the rapid proliferation of file encryption on the network caused by ransomware can be locked if the network is organized by segments, rather than being accessible all together.
- Control A.12.2.1 (Controls against malware) – Nevertheless, it is not possible to prevent every type of malware that can attack a company, but anti-malware software is getting better at recognizing and fighting ransomware attacks.
The evolution of ransomware
The evolution of ransomware is predicted by experts to be the largest and most effective attack on our systems of all time. It’s a never-ending battle, which is why we urge you to focus on prevention, implementation of information security structure, and continuous improvement.
The selection of the ISO 27001 controls is based on risk analysis defined by the company in order to protect the confidentiality, integrity, and availability of your information. The risk associated with malware will have to be contemplated in the risk analysis, so that the controls are adequate to effectively combat the threat of ransomware.
ISO 27001 doesn’t focus only on IT controls, but also on controls to ensure awareness of all employees, technical or other, to malware threats. Properly aligned with these threats, ISO 27001 is the ideal tool for protection against ransomware or any other type of malware.





